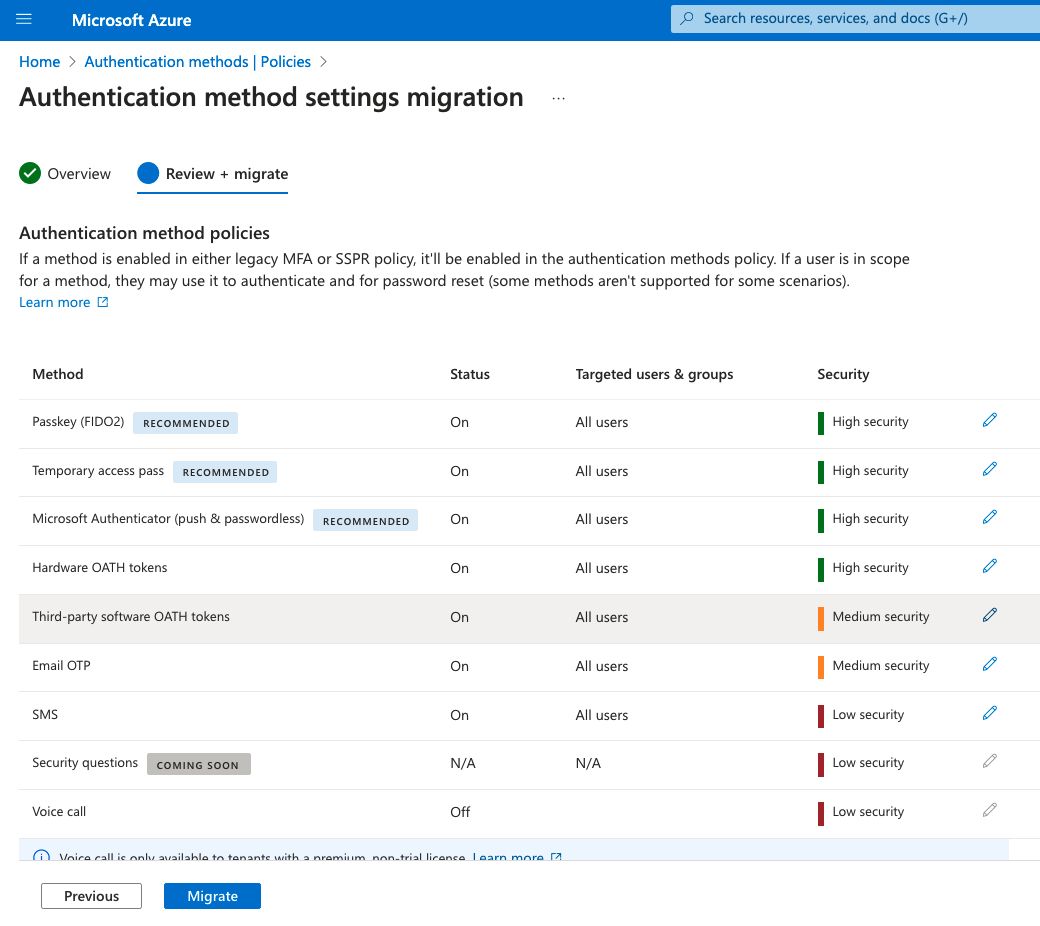
Microsoft Entra ID Authentication: why and how to migrate your methods today
Microsoft Entra ID is evolving – and so should your authentication strategy. Legacy MFA (Multifactor Authentication) and SSPR (Self-Service Password Reset) policies are being retired, with September 30, 2025 set as the final transition date. But waiting on deadlines? Not recommended. Now is the perfect time to use the full potential of Entra ID's modern identity management tools.
Tue, 22 April 2025